Configuring Open ID Connect
Table of contents
Introduction
Connecting identity provider
External Role Assignments Strategy
Role names
Introduction
Note
This feature needs to be unlocked for your account. If you are interested, please contact support@billwerk.com.
OpenID Connect is based on the OAuth 2.0 framework and enables third-party applications to verify the identity of end users and receive basic user profile information. OpenID Connect uses JSON web tokens (JWTs) that you can receive in data flows that conform to the OAuth 2.0 specifications.
Connecting identity provider
Note
To use the single sign-on mechanism, use the URL provided in the Open Id Connect settings in billwerk.
To get to the 3rd party integrations, click on your email address > Settings in the top right corner.
In the BILLWERK APPS section, click 3rd Party Integrations.
In the Open Id Connect row, click the

icon.
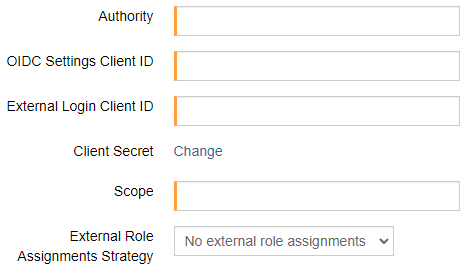
Fill in the required fields.
Click Save.
When Open Id Connect is configured successfully, activate the checkbox.
Click Save.
Field | Description |
|---|---|
Authority | realm URL of the identity provider |
OIDC Settings Client ID | OIDC settings for Client ID from the identity provider for authorization |
External Login Client ID | Client ID from the identity provider for authorization |
Client Secret | Client Secret from the identity provider for authorization |
Scope | identifiers for resources to access |
External Role Assignments Strategy | Strategy for role assignment |
External Role Assignments Strategy
The external role assignment strategy has to be configured in the 3rd Party Integrations in billwerk. To assign roles of billwerk by the identity provider, the claims need to be set in the identity provider.
Note
The token claim name cannot be customized.
External Role Assignments Strategy | Description | Claims |
|---|---|---|
No external role assignments | Roles provided by Identity Provider are not taken into account. Roles can be assigned by admin or during user invitation. | |
One role for all legal entities | Roles provided by Identity Provider are assigned. Roles cannot be assigned by admin or during user invitation. The assignment is done by using custom claims. |
NoteYou can combine roles by separating the role names with two hashtags. Example "roles:billwerk":"Finance" "roles:billwerk":"Finance##Products" |
Example "extn.tenant_id":"64c6db2dd86a3dc43db81cf6" | ||
Role per legal entity | NoteOnly available with the multi tenant feature in combination with Open Id Connect. Roles provided by Identity Provider are assigned. Roles cannot be assigned by admin or during user invitation. The assignment is done by using custom claims. The claim must contain the entity Id. |
NoteYou can combine roles by separating the role names with two hashtags. Example "roles:billwerk":"Finance:62c6db2da85a7dc43db81cf6" |
Role names
The role name must be used in the claim to assign the corresponding role.
Role name | Role |
|---|---|
Admin | Admin |
Operations | Operations |
Finance | Finance |
Products | Products |
ReadOnlyOperations | ReadOnlyOperations |
Reports | Reports |
Templates | Templates |